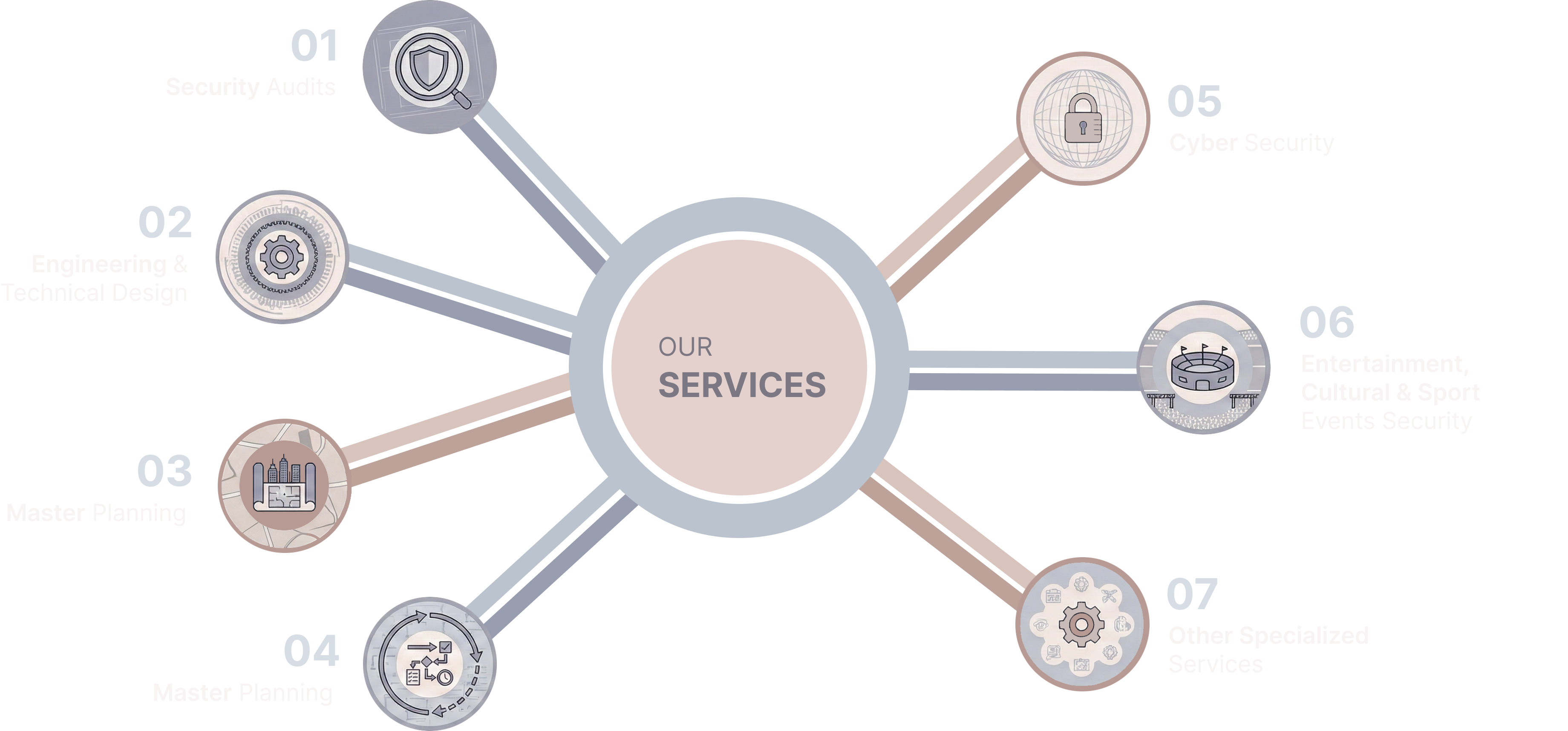
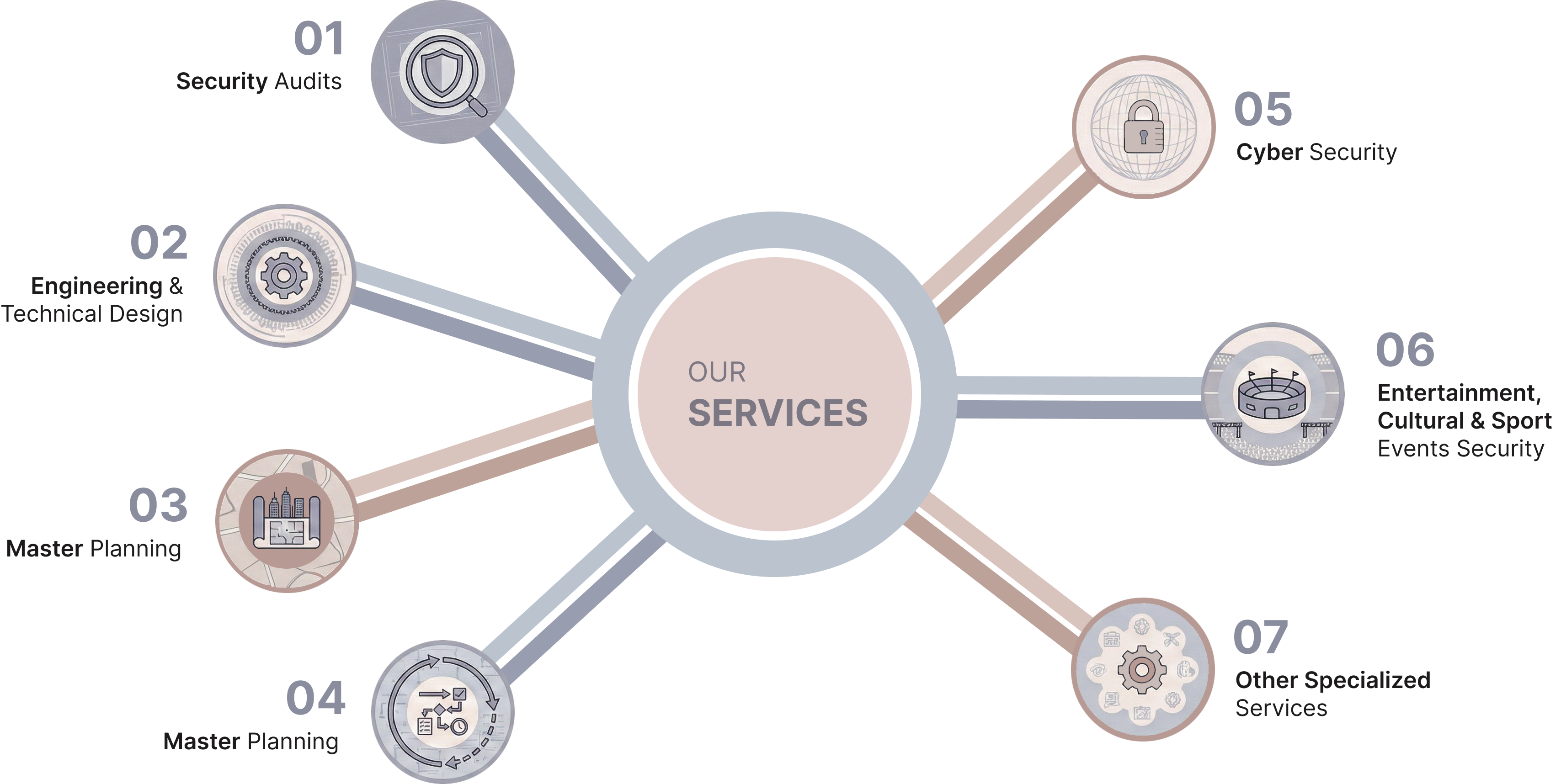
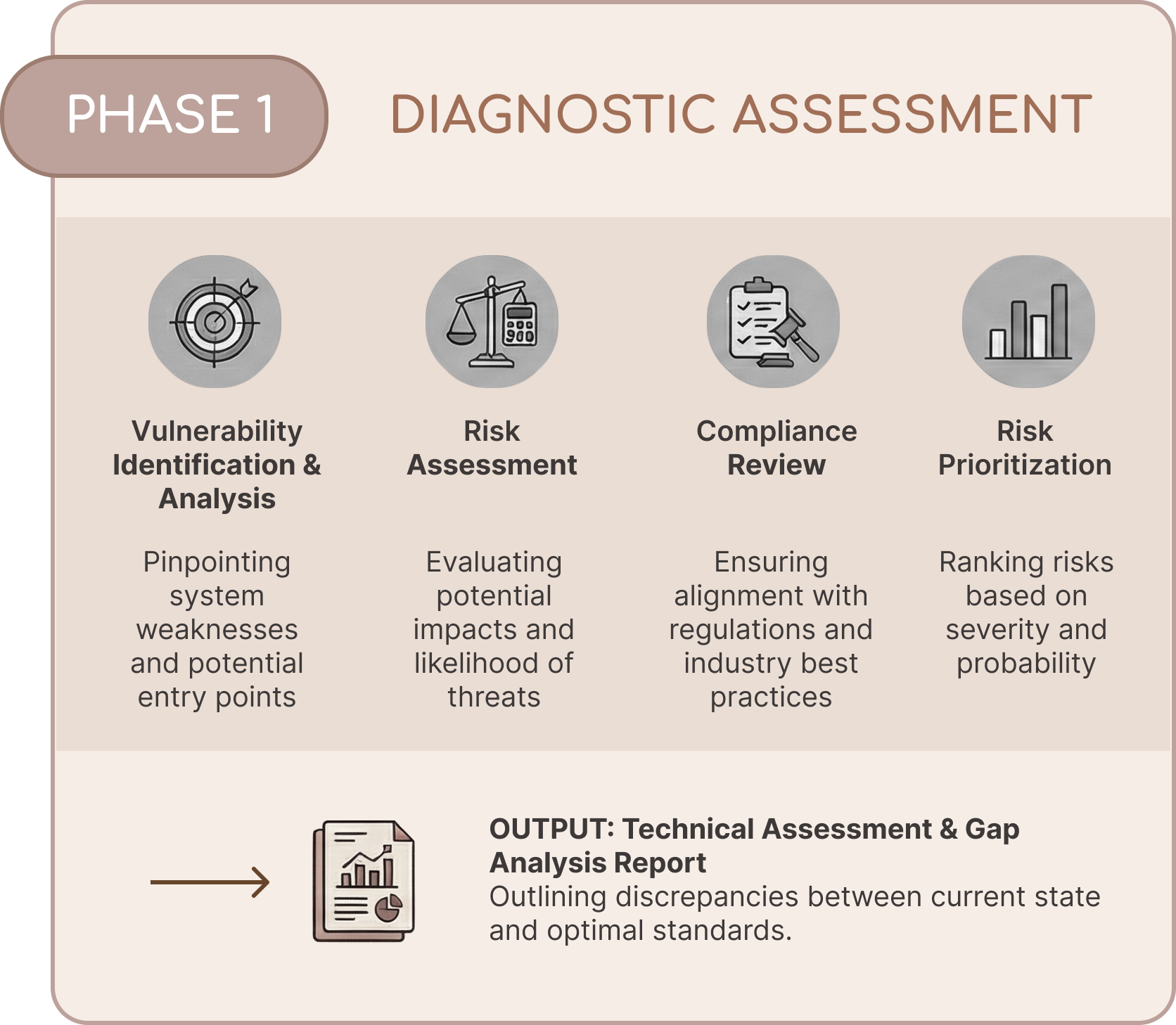
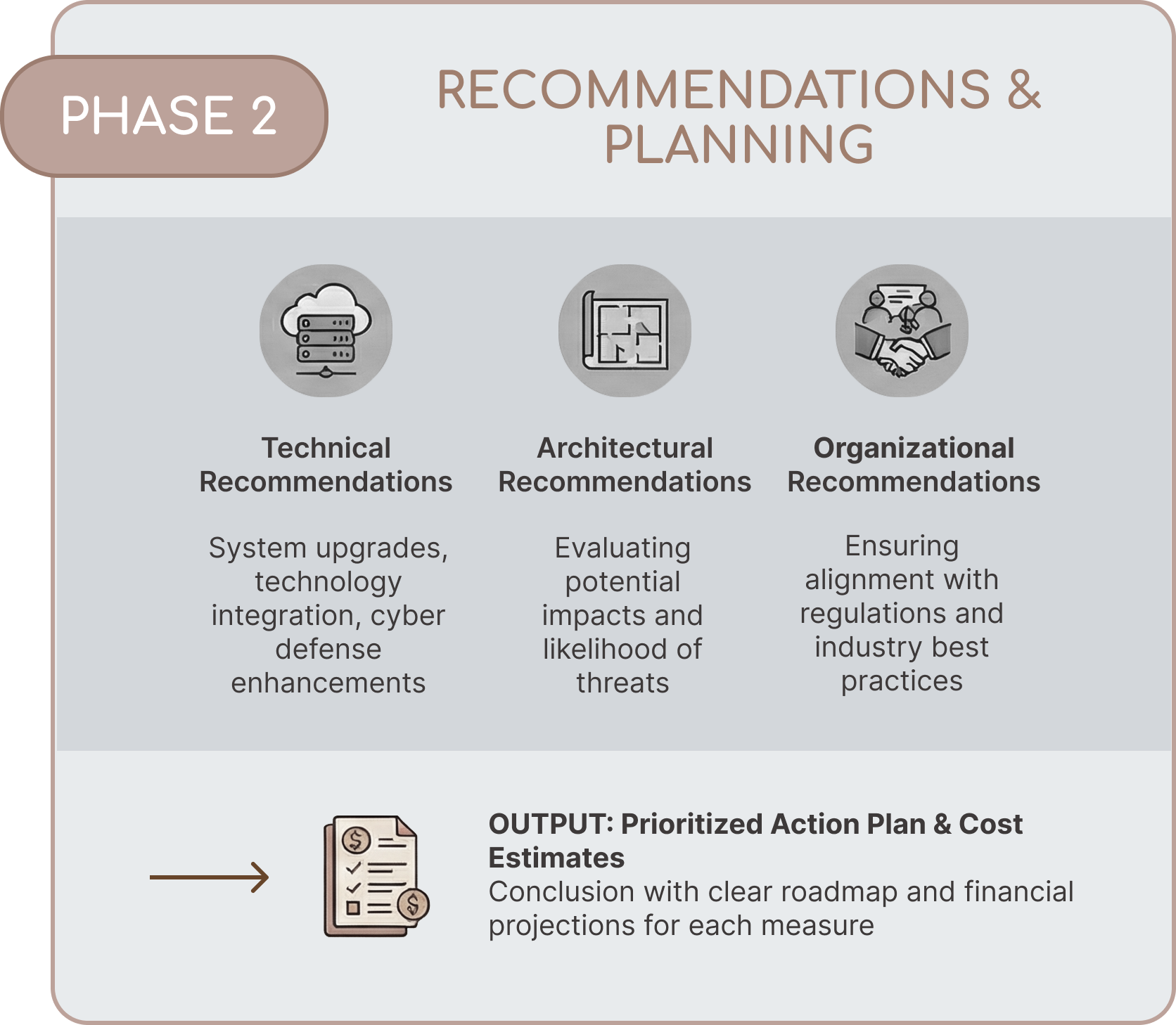
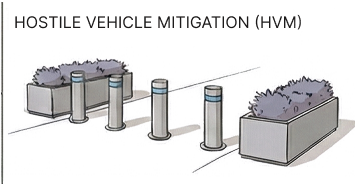
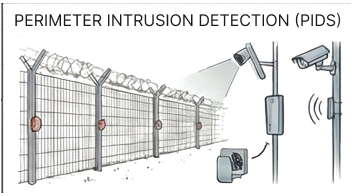
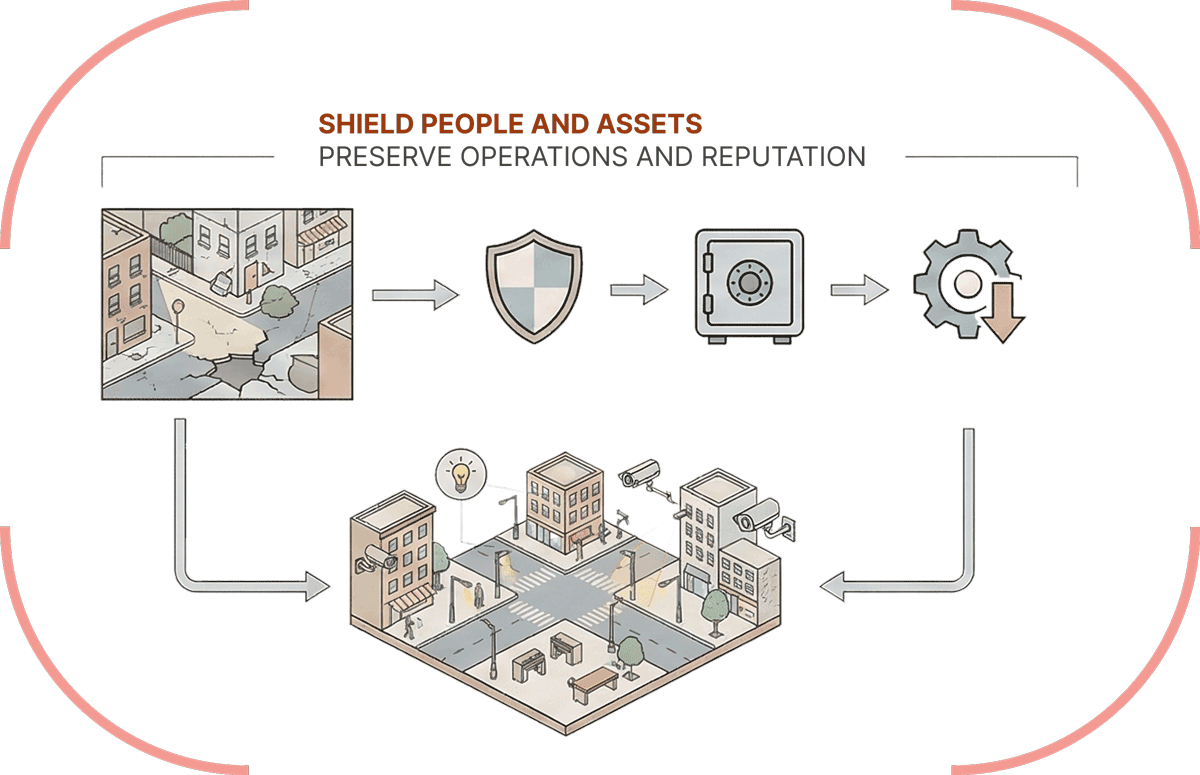
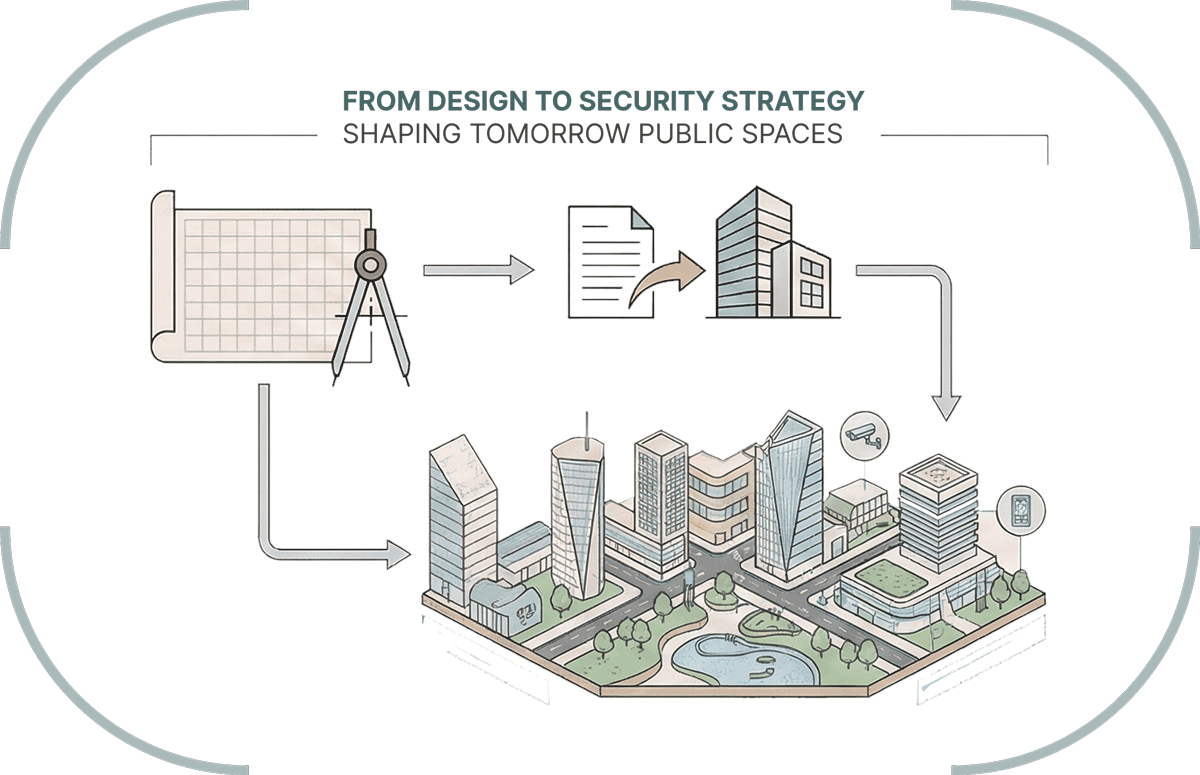
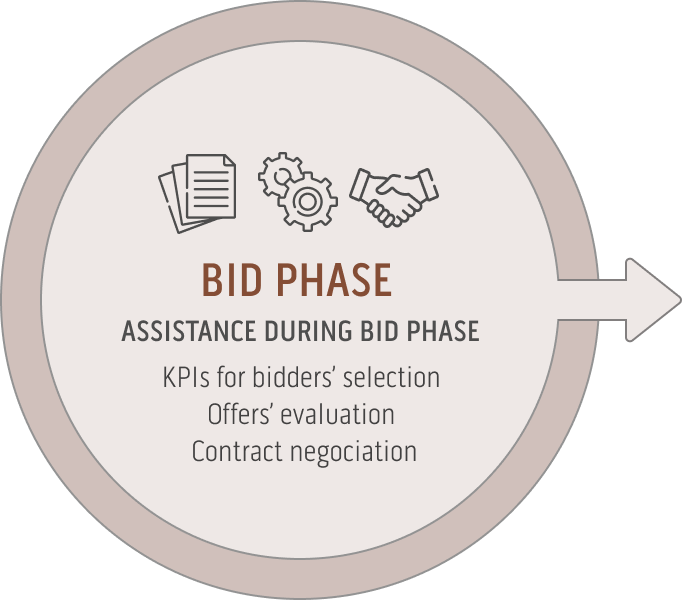
Our Service Offering
From government ministries and local authorities to social housing providers, major event organisers and private operators, more than 1000 clients trust Cronos to anticipate, prevent and manage security risks and to design solutions that fit their reality on the ground.